[ad_1]
As the price of cryptocurrency increases so does the volume of illicit mining detected in the wild, researchers say.
Cryptocurrency has become a favored means for many threat actors to monetize cyberattacks. While, perhaps, the most well-known application of crypto including Bitcoin (BTC), Ethereum (ETH), and Monero (XMR) in the criminal realm is when ransomware payments are made, more covertly, cryptocurrency mining is also a problem.
Cryptocurrency mining malware, when deployed on PCs or unsecured servers, quietly siphons away computing resources to generate virtual currency which is then sent to wallets controlled by its operators.
Also known as cryptojacking, the most common forms of this malware — which may start out as legitimate programs before being twisted for criminal purposes — in the wild include Coinhive, Jsecoin, XMRig, and Cryptoloot.
Cyberattackers will look for the best returns for their time, and in an examination of the topic published on Wednesday, researchers from Cisco Talos attempted to define the links between cryptojacking rates and cryptocurrency prices.
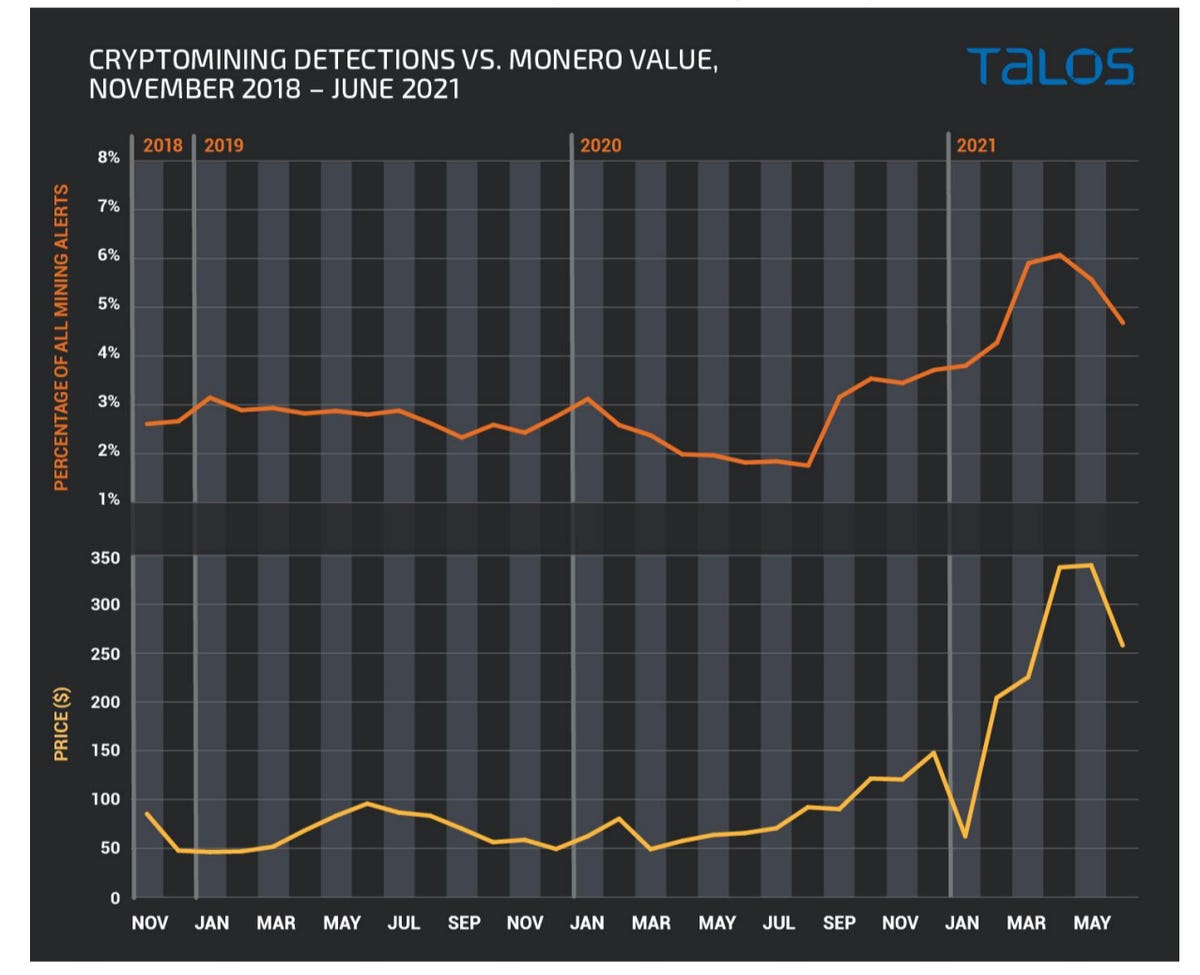
Monero was chosen as the cryptocurrency of interest and cryptomining activity for this coin, against its value, between November 2018 and June 2021, was analyzed.
“Monero is a favorite for illicit mining for a variety of reasons, but two key points are: It’s designed to run on standard, non-specialized, hardware, making it a prime candidate for installation on unsuspecting systems of users around the world, and it’s privacy-focused,” the researchers say.
Talos notes that while the value of this cryptocurrency has fluctuated over the years — indeed, like many others — its price increased from late 2020 to now, when it has experienced a pullback.
The researchers then applied network-based cryptojacking detection tools which monitored Monero in millions of events associated with cryptocurrency mining.
According to the team, not only were they “floored” to see how much more common cryptojacking is since 2018, but also, outside of the price drop in early 2021, “the graph tracks almost identically to the value of the currency.”
Cisco Talos
“This was honestly a pretty surprising correlation since it’s believed that malicious actors need a significant amount of time to set up their mining operations, so it’s unlikely they could flip a switch overnight and start mining as soon as values rise,” Talos says. “This may still be true for some portion of the threat actors deploying miners, but based on the actual data, there are many others chasing the money.”
However, considering crackdowns on cryptocurrency mining and trading around the world, if the cryptojacking environment becomes more difficult or less lucrative, it is entirely possible that threat actors will turn their attention to the next big thing.
“Detection for cryptomining can be spread into a variety of different places including blocking mining-related domains, to enforcing limitations on the end system preventing the mining from starting and lots of network-based detection, which this research is based on,” Talos says. “Regardless of the detection point, organizations should be working to prevent it.”
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
[ad_2]


